Inbound connections that do not match a rule are blocked. This is a critical security measure that can help to protect your network from unauthorized access. By default, all inbound connections that do not match a rule are dropped. This means that only traffic that is explicitly allowed by a rule will be able to enter your network.
There are many different types of inbound connection block rules. Some common examples include:
Inbound Connection Block Rules
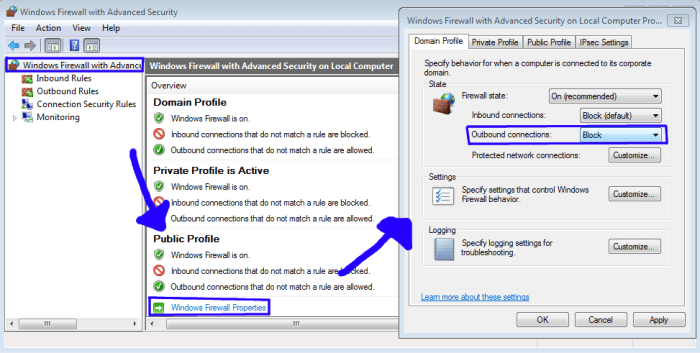
Inbound connection block rules are security measures that restrict incoming connections to a computer or network based on predefined criteria. They are used to protect against unauthorized access, malicious attacks, and other security threats.
Common inbound connection block rules include:
- Blocking connections from specific IP addresses or ranges
- Blocking connections from specific ports or port ranges
- Blocking connections from specific protocols
Inbound connection block rules provide several benefits, including:
- Enhanced security by preventing unauthorized access and malicious attacks
- Reduced network traffic by blocking unnecessary or unwanted connections
- Improved performance by reducing the load on network resources
Types of Inbound Connections
There are several different types of inbound connections, each with its own characteristics:
- TCP connections: TCP (Transmission Control Protocol) connections are reliable and ordered, ensuring that data is transmitted and received correctly.
- UDP connections: UDP (User Datagram Protocol) connections are unreliable and unordered, but they are faster and more efficient than TCP connections.
- ICMP connections: ICMP (Internet Control Message Protocol) connections are used to send error messages and other control information between devices.
To distinguish between different types of inbound connections, you can use tools such as netstat or Wireshark.
Consequences of Blocking Inbound Connections
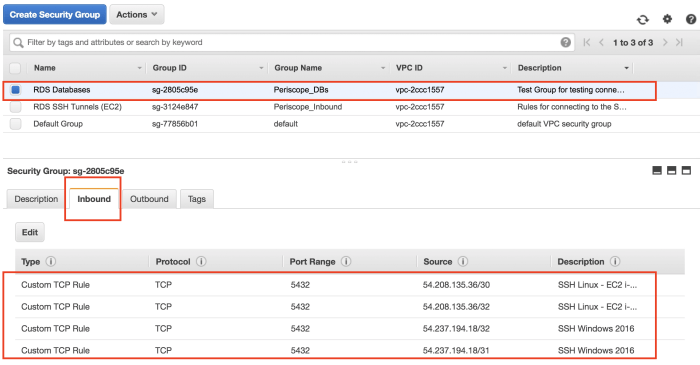
Blocking inbound connections can have several negative consequences, including:
- Denial of service: Blocking legitimate connections can prevent users from accessing essential services or resources.
- Network segmentation: Blocking inbound connections can isolate devices or networks from the rest of the world.
- Performance degradation: Blocking unnecessary connections can improve performance, but blocking legitimate connections can slow down network traffic.
To mitigate these risks, it is important to carefully consider the potential consequences of blocking inbound connections before implementing them.
Best Practices for Managing Inbound Connections
To effectively manage inbound connections, it is important to follow best practices such as:
- Regularly review inbound connection block rules: Ensure that rules are up-to-date and still relevant.
- Use a firewall: A firewall can block inbound connections based on predefined rules.
- Use intrusion detection and prevention systems: These systems can detect and block malicious inbound connections.
- Monitor network traffic: Regularly monitor network traffic to identify suspicious or unauthorized connections.
By following these best practices, you can effectively manage inbound connections and protect your network from security threats.
Tools for Managing Inbound Connections
There are several tools that can be used to manage inbound connections, including:
- Firewalls: Firewalls can block inbound connections based on predefined rules.
- Intrusion detection and prevention systems (IDS/IPS): IDS/IPS systems can detect and block malicious inbound connections.
- Network monitoring tools: Network monitoring tools can be used to identify suspicious or unauthorized inbound connections.
The best tool for managing inbound connections will depend on your specific needs and requirements.
Inbound Connection Block Rules in Practice
Inbound connection block rules are used in a variety of real-world applications, including:
- Protecting against DDoS attacks: Inbound connection block rules can be used to block malicious traffic from DDoS attacks.
- Preventing unauthorized access: Inbound connection block rules can be used to block connections from unauthorized users or devices.
- Enhancing network performance: Inbound connection block rules can be used to block unnecessary or unwanted connections, which can improve network performance.
By implementing inbound connection block rules, organizations can protect their networks from security threats, improve performance, and prevent unauthorized access.
Future Trends in Inbound Connection Blocking
The future of inbound connection blocking is likely to be shaped by several emerging trends, including:
- Increased use of artificial intelligence (AI): AI can be used to detect and block malicious inbound connections more effectively.
- Development of new blocking techniques: New blocking techniques are being developed to address the evolving threat landscape.
- Increased focus on cloud security: As more organizations move their infrastructure to the cloud, there will be an increased need for cloud-based inbound connection blocking solutions.
By staying up-to-date on these trends, organizations can ensure that their inbound connection blocking strategies are effective and up-to-date.
FAQ: Inbound Connections That Do Not Match A Rule Are Blocked
What are inbound connections?
Inbound connections are connections that originate from outside your network and are directed to a computer or device within your network.
What are firewall rules?
Firewall rules are a set of criteria that define which inbound and outbound connections are allowed or denied.
Why is it important to block inbound connections that do not match a rule?
Blocking inbound connections that do not match a rule helps to protect your network from unauthorized access and data breaches.